Fabian Tech Tips

VPN: A Comprehensive Guide to Types, Implementation, and Advanced Features
Feb 8
15 min read
0
17
0
VPN: A Comprehensive Guide to Types, Implementation, and Advanced Features
In today's digital age, where our digital footprint expands with every click and connection, the need for online security and privacy has never been greater. Virtual Private Networks (VPNs) have emerged as indispensable tools for individuals and businesses seeking to safeguard their online activities and data from prying eyes. By establishing a secure, encrypted connection between your device and a remote server, a VPN acts as a digital shield, protecting your sensitive information from potential threats and allowing you to bypass geographical restrictions. This comprehensive guide delves deep into the world of VPNs, exploring the different types, their implementation on various devices, troubleshooting common issues, and mastering advanced features like kill switches and split tunneling.
Security Implications of VPNs
While VPNs offer a robust layer of protection for your online activities, it's crucial to understand their potential security implications and make informed decisions about your VPN usage. Here are some key considerations:
VPN Provider Trustworthiness: The foundation of a secure VPN connection lies in the trustworthiness of your VPN provider. Opt for reputable providers with a transparent privacy policy, a strong commitment to user anonymity, and a proven track record of protecting user data1.
Logging Policies: Some VPN providers may log user data, such as browsing history, connection timestamps, and IP addresses. This data could be vulnerable to breaches or be shared with third parties. Prioritize providers with a strict no-logs policy to ensure your online activities remain private3.
DNS Leaks: A Domain Name System (DNS) leak occurs when your device sends DNS requests outside the VPN tunnel, potentially exposing your browsing history to your internet service provider (ISP) or other third parties. Choose a VPN with built-in DNS leak protection to prevent this3.
IP Address Leaks: An IP address leak can reveal your true location even when connected to a VPN. This can happen if the VPN connection drops unexpectedly. A kill switch is essential to prevent IP address leaks by automatically disconnecting your device from the internet if the VPN fails3.
Vulnerabilities: VPN protocols and implementations can have vulnerabilities that attackers might exploit. Keep your VPN software updated to the latest version to benefit from security patches and bug fixes that address these vulnerabilities4.
To illustrate the potential consequences of VPN vulnerabilities, consider a scenario where a company relies on a VPN with weak encryption or outdated protocols. Attackers could exploit these weaknesses to intercept sensitive corporate data, gain unauthorized access to the company's network, or launch further attacks5.
Types of VPNs
VPNs come in various forms, each tailored to specific needs and use cases. Here's a breakdown of the common types:
Remote Access VPN: This is the most prevalent type of VPN, enabling individuals to establish a secure connection to a private network from any location. It's ideal for remote workers, students accessing school resources, or travelers using public Wi-Fi who need to protect their online activities and access geographically restricted content7.
Site-to-Site VPN: This type of VPN interconnects two or more private networks, such as those of different company branches, forming a secure tunnel for seamless data exchange. It's often used to create a unified network infrastructure for organizations with multiple locations, allowing employees to access resources and collaborate securely across different offices7.
Cloud VPN: Designed specifically for cloud environments, this VPN provides secure access to resources, data, and applications hosted in the cloud. It offers rapid worldwide configuration and deployment, making it a suitable choice for businesses with cloud-based operations and a globally distributed workforce7.
SSL VPN: This VPN leverages Secure Sockets Layer (SSL) encryption to establish a secure connection, primarily used to grant access to web-based applications and services. It's often employed by businesses to provide secure remote access to employees who need to access company intranets or web applications from outside the office7.
Double VPN: This method enhances security by routing your connection through two VPN servers instead of one, adding an extra layer of encryption and making it more difficult for anyone to trace your online activities. However, this added security can come at the cost of slower connection speeds due to the increased processing overhead7.
VPN Protocols
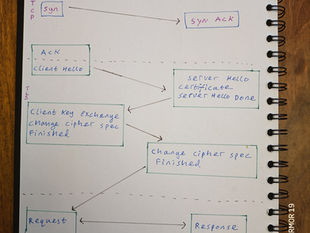
VPNs employ various protocols that dictate how data is transmitted through the encrypted tunnel. Each protocol has its own strengths and weaknesses in terms of speed, security, and compatibility. Here's an overview of the most common VPN protocols:
PPTP (Point-to-Point Tunneling Protocol): As one of the oldest VPN protocols, PPTP is known for its speed and ease of setup. However, it has significant security vulnerabilities and weak encryption standards, making it susceptible to attacks. It is generally not recommended for security-sensitive applications9.
L2TP/IPsec (Layer 2 Tunneling Protocol with Internet Protocol Security): This protocol combines the tunneling capabilities of L2TP with the security features of IPsec, offering a more secure connection than PPTP. It is widely supported by various devices and operating systems, making it a versatile choice for many VPN implementations. However, it's crucial to ensure strong pre-shared keys are used for optimal security11.
OpenVPN: An open-source protocol renowned for its strong security and reliability, OpenVPN is highly configurable and compatible with various encryption algorithms. It utilizes the OpenSSL library, which allows for 256-bit encryption and supports Perfect Forward Secrecy (PFS) for enhanced security14.
WireGuard: A relatively new protocol, WireGuard is gaining popularity due to its lightweight design, faster speeds, and improved performance compared to OpenVPN. It offers strong security features while maintaining efficiency, making it a suitable choice for users who prioritize both speed and security16.
IKEv2 (Internet Key Exchange version 2): This protocol is known for its ability to quickly re-establish connections, making it ideal for mobile users who frequently switch between networks or experience intermittent connectivity. It offers decent security and is often preferred for its resilience in dynamic network environments12.
Choosing the Right Protocol:
Selecting the appropriate VPN protocol depends on your specific needs and priorities. Here's a quick comparison to guide your decision:
Protocol | Speed | Security | Ease of Use | Recommended Use Cases |
OpenVPN | Moderate | High | High | General use, strong security |
WireGuard | High | High | Moderate | Speed-sensitive applications, gaming |
IKEv2/IPSec | Moderate | Moderate | High | Mobile devices, frequent network switching |
L2TP/IPSec | Moderate | Moderate | Moderate | Manual VPN configuration |
PPTP | High | Low | High | Legacy systems, non-critical applications |
Implementing VPN on Different Devices
Setting up a VPN connection might seem daunting, but it's a straightforward process with the right guidance. Here's a step-by-step guide for implementing VPNs on various devices:
Windows
Using a VPN app: Most VPN providers offer dedicated apps for Windows that simplify the setup process.
Download the app from the provider's website or a trusted app store.
Install the app and launch it.
Follow the on-screen instructions to create an account or log in to your existing account.
Select a VPN server location and connect18.
Manual setup: Windows has built-in VPN functionality that allows for manual configuration.
Go to Settings > Network & Internet > VPN.
Click Add a VPN connection.
Choose Windows (built-in) as the VPN provider.
Enter a Connection name.
Provide the Server name or address.
Select the VPN type (e.g., L2TP/IPsec, PPTP).
Choose the Type of sign-in info (e.g., username/password).
Enter your username and password.
Click Save20.
VPN Passthrough: If you're using an older router, you might need to enable VPN passthrough in your router settings. This feature allows VPN traffic to bypass Network Address Translation (NAT) devices, which can sometimes interfere with VPN connections22.
macOS
Using a VPN app: Similar to Windows, most VPN providers offer dedicated apps for macOS.
Download the app from the provider's website or the App Store.
Install the app and launch it.
Follow the on-screen instructions to create an account or log in.
Select a VPN server location and connect23.
Manual setup: macOS also has built-in VPN functionality.
Go to System Preferences > Network.
Click the "+" button to add a new VPN configuration.
Choose the VPN type (e.g., L2TP over IPSec, IKEv2).
Enter a Service name.
Provide the Server address and Account name.
Click Authentication Settings and enter the required information (e.g., password, shared secret).
Click Advanced to configure additional settings (optional).
Click Apply and then OK24.
VPN Passthrough: If necessary, enable VPN passthrough in your router settings to allow VPN traffic to pass through NAT devices22.
Android
Using a VPN app:
Download the VPN app from the Google Play Store.
Install the app and launch it.
Follow the on-screen instructions to create an account or log in.
Select a VPN server location and connect26.
Manual setup: Android has built-in VPN support.
Go to Settings > Network & internet > VPN.
Tap the "+" button to add a VPN.
Enter the VPN name.
Select the VPN type (e.g., PPTP, L2TP/IPsec).
Enter the Server address.
Provide any additional information required (e.g., shared secret).
Tap Save28.
VPN Passthrough: If you encounter connection issues, check your router settings and enable VPN passthrough if necessary22.
iOS
Using a VPN app:
Download the VPN app from the App Store.
Install the app and launch it.
Follow the on-screen instructions to create an account or log in.
Select a VPN server location and connect30.
Manual setup: iOS also has built-in VPN functionality.
Go to Settings > General > VPN.
Tap Add VPN Configuration.
Choose the VPN type (e.g., IKEv2, IPSec, L2TP).
Enter a Description, Server, and Remote ID.
Provide your username and password.
Tap Done30.
VPN Passthrough: If you have an older router, enable VPN passthrough in your router settings to ensure smooth VPN connectivity22.
Troubleshooting VPN Issues
Even with proper setup, you might encounter occasional issues with your VPN connection. Here's a troubleshooting guide to help you resolve common problems:
Connection problems:
Check your internet connection: Ensure you have a stable internet connection by browsing other websites or running a speed test33.
Verify your VPN login credentials: Double-check that you've entered the correct username and password for your VPN account33.
Restart your VPN software or device: Restarting your VPN software or your device can often resolve temporary glitches or connectivity issues33.
Check your firewall settings: Firewalls can sometimes block VPN connections. Configure your firewall settings to allow VPN traffic or temporarily disable the firewall to test if it's the cause of the issue10.
Try connecting to a different VPN server: Server outages or high server load can affect connectivity. Try connecting to a different server location to see if it resolves the issue34.
Update your VPN software: Ensure your VPN software is updated to the latest version. Updates often include bug fixes and performance improvements that can address connection problems33.
Slow speeds:
Change your VPN server location: Connect to a server closer to your physical location to reduce latency and improve speeds36.
Change your VPN protocol: Switch to a faster VPN protocol like WireGuard, which is known for its speed and efficiency36.
Switch between TCP and UDP protocols with OpenVPN: If you're using OpenVPN, try switching between TCP and UDP protocols. UDP is generally faster but less reliable than TCP36.
Restart your device and router: Restarting your devices can clear temporary network issues and improve performance36.
Temporarily disable your security software: Security software can sometimes interfere with VPN connections and slow down speeds. Temporarily disable it to see if it's the cause of the issue36.
Use a wired connection: Wired connections generally offer faster and more stable speeds than Wi-Fi. If possible, connect your device to the internet using an Ethernet cable36.
Advanced VPN Features
VPNs offer a range of advanced features that enhance security, privacy, and flexibility. Here are two essential features to master:
Kill Switch
A kill switch is a critical security feature that acts as a safety net for your VPN connection. It automatically disconnects your device from the internet if the VPN connection drops unexpectedly. This prevents your IP address and online activities from being exposed during VPN failures, ensuring your data remains protected39.
Most VPN apps have a kill switch feature that you can enable in the settings. Some VPNs offer different types of kill switches, each with its own level of control and functionality:
Kill Switch Type | Description | Supported Platforms |
System-level | Blocks all internet traffic when the VPN connection drops. | Windows, macOS, Android, iOS, Linux |
Application-level | Allows you to select specific apps that will be blocked from accessing the internet if the VPN connection drops. | Windows, macOS, Android |
Split Tunneling
Split tunneling provides granular control over your VPN connection by allowing you to route some of your internet traffic through the VPN tunnel while excluding others. This can be useful in various scenarios:
Accessing local network devices: If you need to access devices on your local network, such as printers or shared files, while connected to the VPN, split tunneling allows you to do so without disabling the VPN entirely.
Improving speeds for certain activities: By excluding non-sensitive traffic from the VPN tunnel, you can improve speeds for activities like online gaming or streaming, where latency can be critical.
Accessing geographically restricted content: You can use split tunneling to access content from your home country while connected to a VPN server in another location.
You can configure split tunneling in your VPN app settings by selecting the apps or websites that you want to exclude from the VPN connection41.
Reputable VPN Providers
Choosing the right VPN provider is crucial for a secure and reliable VPN experience. Consider factors such as security features, speed, server locations, pricing, and user reviews when making your decision. Here's a comparison of some reputable VPN providers:
Provider | Features | Pricing | Server Locations | User Reviews |
NordVPN | 256-bit AES encryption, 5500+ servers, kill switch, split tunneling, Threat Protection | $3.39 - $12.99/month | 60 countries | Generally positive, known for speed and security. Some concerns about limited city options and Linux client interface44. |
Surfshark | 256-bit AES encryption, 3200+ servers, kill switch, split tunneling, CleanWeb, unlimited devices | $2.19 - $15.45/month | 100 countries | Positive reviews for speed, affordability, and unlimited devices. Some users find the apps cluttered49. |
Private Internet Access | 128-bit to 256-bit AES encryption, 35912+ servers, kill switch, split tunneling, MACE ad blocker | $2.03 - $11.95/month | 84 countries | No specific user review information available. |
Hotspot Shield | Hydra Catapult protocol, 1800+ servers, kill switch, split tunneling, malware protection | $7.99 - $12.99/month | 80+ countries | Mixed reviews. Praised for speed and streaming capabilities, but some concerns about IP leaks and limited payment options50. |
UltraVPN | Hydra Catapult protocol, 1000+ servers, kill switch, split tunneling, malware and phishing protection | $2.99 - $7.99/month | 120+ cities | Mixed reviews. Some users report good speeds and ease of use, while others experience slow speeds and IP leaks55. |
User Reviews
Here's a summary of user feedback on some of the VPN providers mentioned above:
NordVPN: Users generally praise NordVPN for its speed, security features, and ease of use. Some users appreciate the Threat Protection feature, while others highlight the extensive server network and reliable customer support. However, some concerns have been raised about limited city options in smaller countries and the lack of a graphical interface for the Linux client44.
Hotspot Shield: User reviews on Hotspot Shield are mixed. Some users appreciate its speed and streaming capabilities, while others report issues with IP address leaks and limited payment options. The free version is generally well-regarded for its unlimited data, but the paid version offers better performance and features50.
UltraVPN: UltraVPN receives mixed feedback from users. Some users praise its speed and ease of use, while others report slow speeds and occasional IP address leaks. The user-friendly interface and affordability are often highlighted, but the lack of open-source protocols and the limited server network are potential drawbacks55.
Conclusion
VPNs are essential tools for navigating the digital landscape securely and privately. By understanding the different types of VPNs, their implementation, troubleshooting techniques, and advanced features, you can make informed decisions to protect your online activities and access content from anywhere in the world. Remember to choose a reputable VPN provider, prioritize security when configuring your VPN connection, and stay informed about potential security implications. Start your journey towards enhanced online security and privacy by exploring the VPN options and resources discussed in this guide.
Works cited
1. Dangers When Using a VPN: Everything You Should Know - Devoteam, accessed on February 8, 2025, https://www.devoteam.com/expert-view/dangers-of-vpn-security-risks-privacy-concerns/
2. VPN Security Concerns in 2025 - UpGuard, accessed on February 8, 2025, https://www.upguard.com/blog/vpn-risk
3. VPN Security Risks: How to Safeguard Your Data - SentinelOne, accessed on February 8, 2025, https://www.sentinelone.com/cybersecurity-101/cybersecurity/vpn-security-risks/
4. 5 Biggest VPN Security Risks - Check Point Software Technologies, accessed on February 8, 2025, https://www.checkpoint.com/cyber-hub/network-security/what-is-vpn/5-biggest-vpn-security-risks/
5. VPN Security: Are VPNs Safe and Secure? - Palo Alto Networks, accessed on February 8, 2025, https://www.paloaltonetworks.com/cyberpedia/vpn-security
6. VPN security: How VPNs help secure data and control access - Cloudflare, accessed on February 8, 2025, https://www.cloudflare.com/learning/access-management/vpn-security/
7. What Are the Different Types of VPN? - Palo Alto Networks, accessed on February 8, 2025, https://www.paloaltonetworks.com/cyberpedia/types-of-vpn
8. Different types of VPN protocols & when to use them - NordLayer, accessed on February 8, 2025, https://nordlayer.com/learn/vpn/types-and-protocols/
9. What Is PPTP (Point-to-Point Tunneling Protocol)? - Palo Alto Networks, accessed on February 8, 2025, https://www.paloaltonetworks.com/cyberpedia/what-is-pptp
10. What is the PPTP (Point-to-Point Tunneling Protocol)? - NordVPN, accessed on February 8, 2025, https://nordvpn.com/blog/what-is-pptp-protocol/
11. www.paloaltonetworks.com, accessed on February 8, 2025, https://www.paloaltonetworks.com/cyberpedia/what-is-l2tp#:~:text=L2TP%20is%20often%20paired%20with,for%20its%20enhanced%20security%20measures.
12. What is the Layer 2 Tunneling Protocol (L2TP)? - NordVPN, accessed on February 8, 2025, https://nordvpn.com/blog/l2tp-protocol/
13. What Is L2TP (Layer 2 Tunnel Protocol)? - Palo Alto Networks, accessed on February 8, 2025, https://www.paloaltonetworks.com/cyberpedia/what-is-l2tp
14. OpenVPN - Wikipedia, accessed on February 8, 2025, https://en.wikipedia.org/wiki/OpenVPN
15. OpenVPN: Business VPN For Secure Networking, accessed on February 8, 2025, https://openvpn.net/
16. Types of VPNs and when to use them - Surfshark, accessed on February 8, 2025, https://surfshark.com/blog/types-of-vpns
17. Types of VPN Protocols: Explanation and Comparison - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/protocols/
18. A How-to Guide for Setting up a VPN on Windows 10 | Security.org, accessed on February 8, 2025, https://www.security.org/vpn/windows-10-setup/
19. How to set up a VPN: A step-by-step guide | NordVPN, accessed on February 8, 2025, https://nordvpn.com/blog/how-to-set-up-a-vpn/
20. Connect to a VPN in Windows - Microsoft Support, accessed on February 8, 2025, https://support.microsoft.com/en-us/windows/connect-to-a-vpn-in-windows-3d29aeb1-f497-f6b7-7633-115722c1009c
21. Windows-10-VPN-Setup - Information Technology | UWSP, accessed on February 8, 2025, https://www3.uwsp.edu/infotech/Pages/Tutorials/VPN/Windows-10-VPN-Setup.aspx
22. What Is PPTP (Point-To-Point Tunneling Protocol)? - ExpressVPN, accessed on February 8, 2025, https://www.expressvpn.com/what-is-vpn/protocols/pptp
23. How to Install and Use a VPN on a Mac in 2025 - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/mac/
24. support.apple.com, accessed on February 8, 2025, https://support.apple.com/guide/mac-help/set-up-a-vpn-connection-on-mac-mchlp2963/mac#:~:text=On%20your%20Mac%2C%20choose%20Apple,may%20need%20to%20scroll%20down.)&text=Click%20the%20Action%20pop%2Dup,you%20want%20to%20set%20up.
25. Set up a VPN connection on Mac - Apple Support, accessed on February 8, 2025, https://support.apple.com/guide/mac-help/set-up-a-vpn-connection-on-mac-mchlp2963/mac
26. VPN for Android: What it is and how to set it up - NordVPN, accessed on February 8, 2025, https://nordvpn.com/blog/vpn-for-android/
27. How to Set Up a VPN on Android: Quick Guide - Private Internet Access, accessed on February 8, 2025, https://www.privateinternetaccess.com/blog/set-up-vpn-android/
28. Connect to a virtual private network (VPN) on Android - Google Help, accessed on February 8, 2025, https://support.google.com/android/answer/9089766?hl=en
29. How to Setup a VPN on Android Phones & Devices in 2025 - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/android/
30. How to Set Up a VPN on an iPhone in 2025 - McAfee, accessed on February 8, 2025, https://www.mcafee.com/learn/how-to-set-up-a-vpn-on-an-iphone/
31. How to use a VPN on iPhone or iPad in 2025 - Norton, accessed on February 8, 2025, https://us.norton.com/blog/mobile/how-to-use-vpn-on-iphone
32. www.mcafee.com, accessed on February 8, 2025, https://www.mcafee.com/learn/how-to-set-up-a-vpn-on-an-iphone/#:~:text=Tap%20on%20your%20%E2%80%9CSettings%E2%80%9D%20app,Tap%20%E2%80%9CAdd%20VPN%20Configuration.%E2%80%9D
33. How to Fix VPN Problems - Kaspersky, accessed on February 8, 2025, https://www.kaspersky.com/resource-center/preemptive-safety/common-vpn-problems
34. Troubleshooting and Fixing Common VPN Issues - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/fix-common-issues/
35. VPN Not Connecting? 9 Steps to Fix Common Issues | ExpressVPN Blog, accessed on February 8, 2025, https://www.expressvpn.com/blog/vpn-not-connecting/
36. Slow VPN? Try these 8 tips to speed it up - Surfshark, accessed on February 8, 2025, https://surfshark.com/blog/tips-on-how-to-boost-vpn-speed
37. My VPN is slow, what can I do to make it faster? - IVPN Help, accessed on February 8, 2025, https://www.ivpn.net/knowledgebase/troubleshooting/my-vpn-is-slow-what-can-i-do-to-make-it-faster/
38. Yes, a VPN Slows Your Internet—Here's What to Do About It | HighSpeedInternet.com, accessed on February 8, 2025, https://www.highspeedinternet.com/resources/will-a-vpn-slow-down-your-internet
39. What is a VPN Kill Switch? Do you Need it? - Cybernews, accessed on February 8, 2025, https://cybernews.com/what-is-vpn/vpn-kill-switch/
40. VPN Kill Switch: What It Is and Why You Need It - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/kill-switch/
41. What is VPN Split Tunneling ? | Perimeter 81, accessed on February 8, 2025, https://www.perimeter81.com/glossary/vpn-split-tunneling
42. What is VPN split tunneling, and how does it work? - NordVPN, accessed on February 8, 2025, https://nordvpn.com/features/split-tunneling/
43. How to use split tunneling | Proton VPN, accessed on February 8, 2025, https://protonvpn.com/support/protonvpn-split-tunneling
44. NordVPN Reviews - Pros & Cons, Ratings & more - GetApp, accessed on February 8, 2025, https://www.getapp.com/security-software/a/nordvpn/reviews/
45. My Honest NordVPN Review (After 1 Year of Use), accessed on February 8, 2025, https://jussihyvarinen.com/nordvpn-review/
46. NordVPN Review 2025: In-depth Analysis - Cybernews, accessed on February 8, 2025, https://cybernews.com/best-vpn/nordvpn-review/
47. NordVPN Review 2025: A Top VPN Tested by Experts | Security.org, accessed on February 8, 2025, https://www.security.org/vpn/nordvpn/review/
48. NordVPN Review: An In-Depth Analysis From a Long-Time User - Reddit, accessed on February 8, 2025, https://www.reddit.com/r/vpnreviews/comments/1ffuxyh/nordvpn_review_an_indepth_analysis_from_a/
49. The best VPN service 2025 - TechRadar, accessed on February 8, 2025, https://www.techradar.com/vpn/best-vpn
50. Hotspot Shield Review 2025: Is It Really Free and Fast, accessed on February 8, 2025, https://www.vpnmentor.com/reviews/hotspot-shield/
51. Hotspot Shield Reviews | Expert VPN Reviews & User Ratings, accessed on February 8, 2025, https://www.hotspotshield.com/reviews/
52. Hotspot Shield VPN Review 2025 — Is This "Free" VPN Safe? - CyberInsider, accessed on February 8, 2025, https://cyberinsider.com/vpn/reviews/hotspot-shield/
53. Hotspot Shield Review 2025 - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/hotspot-shield/review/
54. Hotspot Shield VPN review - TechRadar, accessed on February 8, 2025, https://www.techradar.com/reviews/hotspot-shield-vpn
55. UltraVPN Review 2025: Initially Cheap, but Is It Any Good? - vpnMentor, accessed on February 8, 2025, https://www.vpnmentor.com/reviews/ultravpn/
56. UltraVPNs Reviews and Ratings, accessed on February 8, 2025, https://ultravpn.com/review/
57. VPN Secure Proxy: UltraVPN™ 4+ - App Store, accessed on February 8, 2025, https://apps.apple.com/us/app/vpn-secure-proxy-ultravpn/id1053874290
58. UltraVPN Review and Pricing Plans 2025 - Security.org, accessed on February 8, 2025, https://www.security.org/vpn/ultravpn/
59. UltraVPN Review 2025: How Good Is It? - Cybernews, accessed on February 8, 2025, https://cybernews.com/best-vpn/ultravpn-review/
60. Best VPN of 2025: Services Tested and Reviewed | Security.org, accessed on February 8, 2025, https://www.security.org/vpn/best/
61. The best VPN service in 2025 - Tom's Guide, accessed on February 8, 2025, https://www.tomsguide.com/best-picks/best-vpn
62. Get the best VPN service for all your needs - Surfshark, accessed on February 8, 2025, https://surfshark.com/vpn
63. Best VPN for 2025: Tested and Recommended by Experts - Cybernews, accessed on February 8, 2025, https://cybernews.com/best-vpn/